당신은 주제를 찾고 있습니까 “스팸 하우스 – IP 양식 블랙리스트를 제거하는 방법 | 스팸하우스 | CBL | 2022년 업데이트됨“? 다음 카테고리의 웹사이트 ppa.maxfit.vn 에서 귀하의 모든 질문에 답변해 드립니다: https://ppa.maxfit.vn/blog. 바로 아래에서 답을 찾을 수 있습니다. 작성자 All Technical Services 이(가) 작성한 기사에는 조회수 5,160회 및 좋아요 29개 개의 좋아요가 있습니다.
스팸 하우스 주제에 대한 동영상 보기
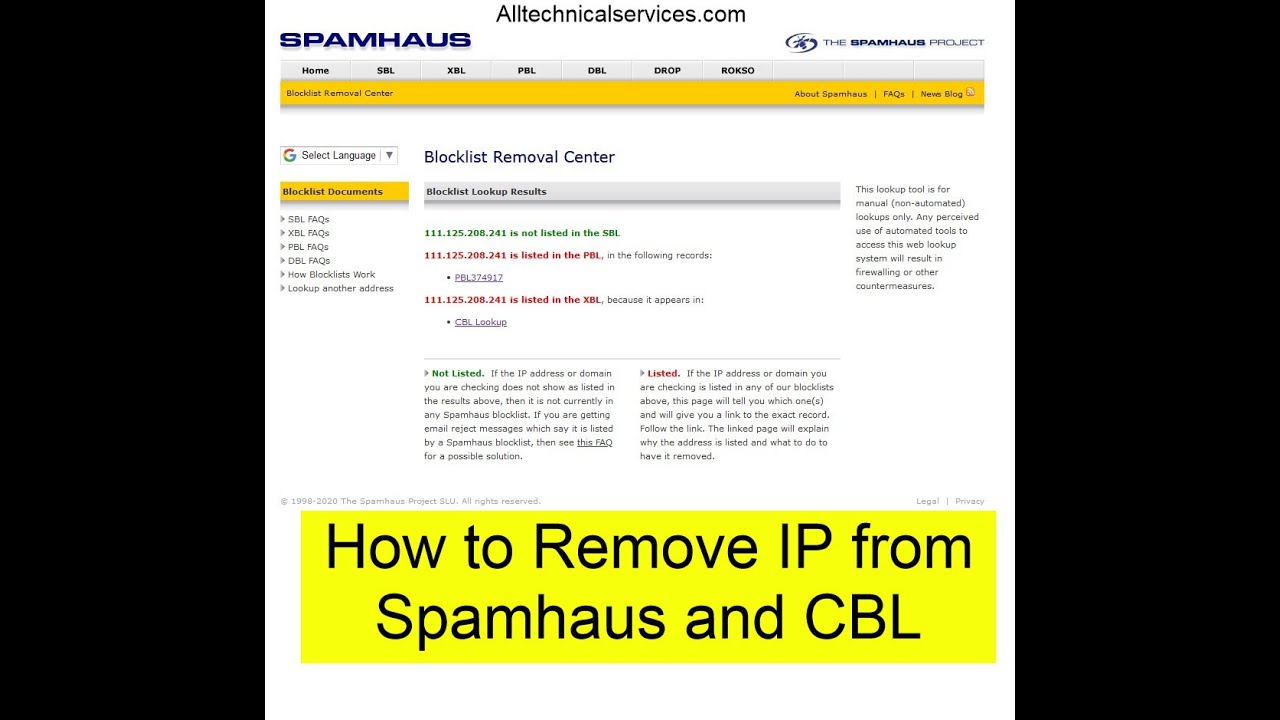
여기에서 이 주제에 대한 비디오를 시청하십시오. 주의 깊게 살펴보고 읽고 있는 내용에 대한 피드백을 제공하세요!
d여기에서 IP 양식 블랙리스트를 제거하는 방법 | 스팸하우스 | CBL | 2022년 업데이트됨 – 스팸 하우스 주제에 대한 세부정보를 참조하세요
How to Remove IP form Blacklist | Spamhaus | CBL?
In this video I have guide you the step by step process to delist your IP or domain from Spamhaus as well as from CBL.
For more details please check my post in which I have explained in details why your IP is blacklisted by Spamhaus and how to remove it step by step.
https://www.alltechnicalservices.com/how-to-remove-ip-from-spamhaus/
If your domain or IP is blacklist by other blacklists then please check my video on how to remove any blacklist yourself.
https://youtu.be/uLS9tl3_wdw
Disclaimer:
==============
This channel may use some copyrighted materials without the specific authorization of the owner but the contents used here falls under the \”Fair Use\”. Copyright Disclaimer under Section 107 of the Copyright Act 1976, allowance is made for \”fair use\” for purposes such as criticism, comment, news reporting, teaching, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational, or personal use tips the balance in favor of fair use.
==============
Copyright:
==============
In case of any copyrighted content please email us we will check and remove it as soon as possible.
==============
스팸 하우스 주제에 대한 자세한 내용은 여기를 참조하세요.
The Spamhaus Project
Spamhaus is the world leader in supplying realtime highly accurate threat intelligence to the Internet’s major networks.
Source: www.spamhaus.org
Date Published: 12/10/2022
View: 3663
스팸하우스, CBL 등 으로 인한 메일발송 장애 문의합니다
안녕하세요. 전산팀에서 근무중인 신입사원입니다. https://www.spamhaus.org와 http://www.abuseat.org 에서 스팸으로 인식하여 그룹…
Source: www.sharedit.co.kr
Date Published: 2/2/2021
View: 1965
Spamhaus Technology: Leaders in IP and domain reputation …
Industry leading IP and domain reputation data to protect emails, networks and prove insight. We protect against cyber threats.
Source: www.spamhaus.com
Date Published: 12/22/2022
View: 989
The Spamhaus Project – Wikipedia
The Spamhaus Project is an international organisation based in the Principality of Andorra, founded in 1998 by Steve Linford to track email spammers and …
Source: en.wikipedia.org
Date Published: 4/14/2021
View: 2410
스팸하우스, “DNS-over-HTTPS가 봇넷 추적을 어렵게 만든다
안티스팸 연구를 진행하는 단체인 스팸하우스(Spamhaus)가 DNS-over-HTTPS라는 기술 때문에 봇넷의 추적이 어려워진다고 발표했다.
Source: www.boannews.com
Date Published: 5/21/2022
View: 9709
메일 발송 차단 해지 가이드 – 다우오피스
SPAMHAUS의 black list에서 내 IP 확인하기 … RBL(Real-time Blocking List) 실시간 스팸 차단 리스트로 메일 발송 기능을 차단합니다. RBL이란?
Source: daouoffice.com
Date Published: 12/28/2021
View: 2466
주제와 관련된 이미지 스팸 하우스
주제와 관련된 더 많은 사진을 참조하십시오 IP 양식 블랙리스트를 제거하는 방법 | 스팸하우스 | CBL | 2022년 업데이트됨. 댓글에서 더 많은 관련 이미지를 보거나 필요한 경우 더 많은 관련 기사를 볼 수 있습니다.
주제에 대한 기사 평가 스팸 하우스
- Author: All Technical Services
- Views: 조회수 5,160회
- Likes: 좋아요 29개
- Date Published: 2020. 12. 28.
- Video Url link: https://www.youtube.com/watch?v=Xy3RrwNZdEY
The Spamhaus Project
Blocklists
Safe DNSBLs for Safe Filters
Blocklist Removal
Blocked? To check, get info and resolve listings go to
Blocklist Removal Center
To check, get info and resolve listings go to Blocklist Use
DNSBL Usage Terms
How Blocklists Work
스팸하우스(Spamhaus.org) 에서 블럭리스트 검색 및 제거 방법
스팸하우스는 스팸메일 관련 나름 유명한 사이트라서 참조를 많이함.
https://www.spamhaus.org/
사이트 메인 -> Blocklist Removal Center
IP를 입력하고 검색
여기서 해당 아이피가 등록이 되어 있는지 검색을 하면 됨
SBL / PBL / XBL 에 리스트 등록여부를 알려줌
ex)
SBL : Spamhaus 차단 목록 ( “SBL”) 권고는 Spamhaus에서 전자 메일 수락을 권장하지 않는 IP 주소 데이터베이스입니다.
PBL : Spamhaus PBL은 최종 사용자 IP 주소 범위의 DNSBL 데이터베이스로, 해당 고객의 ISP를 위해 특별히 제공되지 않은 SMTP 메일을 인터넷 메일 서버로 전달해서는 안됩니다. PBL은 네트워크가 MTA 이외의 고객 IP 범위에 대해 허용 가능한 사용 정책을 시행하도록 돕습니다.
XBL : XBL (Spamhaus Exploits Block List)은 오픈 프록시 (HTTP, 양말, AnalogX, 윙 에이트 등), 스팸 엔진이 내장 된 웜 / 바이러스 등 불법적 인 제 3 자 공격에 감염된 하이재킹 된 PC의 IP 주소에 대한 실시간 데이터베이스입니다. 그리고 다른 유형의 트로이 목마 악용.
아이피를 검색했을때 PBL 에 등록된걸 확인할 수 있다.
PBL144310 클릭
Remove an IP from PBL 클릭
주의 사항에 대해서 얘기 하고 있습니다.
위의 페이지에 대해서 이해했으면 Remove IP Addresss 클릭
여기서 중요한 부분이 있습니다.
인증을 받기 위해 email 입력부분에 무료 메일을 사용해서는 안됩니다. 이유는 아래와 같습니다.
무료 메일 주소로 PBL IP를 제거 할 수없는 이유는 무엇입니까?
(Gmail, Hotmail 등)PBL 제거 시스템은 Gmail.com, Hotmail.com, Yahoo.com 또는 기타 무료 전자 메일 도메인과 같은 무료 전자 메일 계정에서 오는 제거 요청을 처리하지 않습니다. 무료 이메일 주소를 사용하여 수행 한 제거는 PBL 제거 시스템 보안 검사에 의해 자동으로 무효화됩니다.
PBL 제거를 요청하려면 자신의 도메인에서 실제 주소를 사용해야합니다.
PBL에서 IP 주소를 제거하는 유일한 합법적 인 이유는 IP 주소에 호스트 된 합법적 인 메일 서버가있는 경우이므로 합법적 인 메일 서버 운영자 만 PBL에서 IP를 제거해야합니다 (그리고 엄격하게 메일의 IP 주소 만). 그들이 운영하는 서버). 따라서 셀프 서비스 제거 프로세스는 IP 제거를 요청하는 사람이 IP 주소에서 호스팅되는 메일 서버의 운영자라고 가정합니다. 그 사람은 보통 ‘[email protected]’이 아닌 ‘postmaster’주소를 사용합니다.
모든 합법적 인 메일 서버에는 적절한 호스트 이름이 있으며 서버 운영자는 일반적으로 운영 통신을받는 데 사용되는 역할 주소 (예 : “postmaster”)를 갖습니다. 합법적 인 메일 서버 운영자는 운영 통신을 위해 무료 메일 주소를 사용할 필요가 없습니다. 이러한 이유로 우리는 freemail 주소의 삭제 요청을 의심스러운 것으로 간주하여 처리하지 않습니다.
그리고
다음 단계 : 이 요청을 확인하기 위해 위에서 입력 한 이메일 주소로 확인 이메일이 발송됩니다. 이메일에는 토큰 (5 자리 코드)이 포함되어 있으며이 IP 주소를 등록 해제하려면 2 단계 (요청 확인)에서 입력해야합니다. 이 코드가 없으면 요청을 처리 할 수 없습니다.
스팸하우스 BlockList IP 해제 (PBL)
스팸하우스는 대량 메일, 또는 스팸 의심 메일을 수집해서 해당 IP를 BlockList에 등록하는 인터넷 스팸 추적 단체.
BlockList에 포함되면 운영하고 있는 서버에서 외부로 메일 발송이 안되는 경우가 발생하고 최종 사용자는 개인 메일( Google, Naver 등)로는 수신이 정상적으로 되지만 특정 서버(조직 등) 내의 메일에서는 해당 IP로부터 메일을 간헐적으로 수신하거나 또는 수신할 수 없는 경우가 발생함.
SPAMHAUS: https://www.spamhaus.org/
* 사이트 접속 > Blocklist Removal Center 클릭.
스팸하우스, CBL 등 으로 인한 메일발송 장애 문의합니다
안녕하세요. 전산팀에서 근무중인 신입사원입니다. http://www.abuseat.org 에서 스팸으로 인식하여그룹웨어 사용자들이 메일 발송시 발송실패로 컴플레인을 걸어와self 리스트 제거를 통해서 (그냥 remove 버튼하나 눌렀을뿐인데 제거되더군요) 리스트 를 해제했는데요이게 대체 어떤원리로 등록 과 해제 가 되는지 궁금합니다단순히 발신 아이피 검색 후 하단에 remove를 눌렀을 뿐인데 해제가 된다니 뭔가좀 의심됩니다거기다가 여러 글들을 웹서칭 해보니 원인파악을 제대로 하지않으면 다시 등재된다고 하는데 사실 원인이 정말찾기 어렵네요, 예상으로는 대량메일발송을 가끔 사용자들이 쓰는데 너무 남용해서 그런게 아닐까 싶기도 합니다만 음..고수분들의 관련지식을(경험 또는 노하우를) 듣고자 합니다감사합니다.
Leaders in IP and domain reputation data
What does Spamhaus do?
30 November 2021
I write this article for all of you out there who aren’t deeply embedded in this industry because the people I work with are remarkable. The world should know what they are doing to quietly protect all those who say “Spamwho?” be that your grandma or the network nerd at work.
The Spamhaus Project
Organization targetting email spammers
The Spamhaus Project is an international organisation based in the Principality of Andorra, founded in 1998 by Steve Linford to track email spammers and spam-related activity. The name spamhaus, a pseudo-German expression, was coined by Linford to refer to an Internet service provider, or other firm, which spams or knowingly provides service to spammers.
Anti-spam lists [ edit ]
The Spamhaus Project is responsible for compiling several widely[2] used anti-spam lists. Many[3] internet service providers and email servers use the lists to reduce the amount of spam that reaches their users. In 2006, the Spamhaus services protected 650 million email users, including the European Parliament, US Army, the White House and Microsoft, from billions of spam emails a day.[4]
Spamhaus distributes the lists in the form of DNS-based Blacklists (DNSBLs) and Whitelists (DNSWLs). The lists are offered as a free public service to low-volume mail server operators on the Internet.[5] Commercial spam filtering services and other sites doing large numbers of queries must instead sign up for an rsync-based feed of these DNSBLs, which Spamhaus calls its Datafeed Service.[6] Spamhaus outlines the way its DNSBL technology works in a document called Understanding DNSBL Filtering.[7]
The Spamhaus Block List (SBL)[8] targets “verified spam sources (including spammers, spam gangs and spam support services).” Its goal is to list IP addresses belonging to known spammers, spam operations, and spam-support services.[9] The SBL’s listings are partially based on the ROKSO index of known spammers.
The Exploits Block List (XBL)[10] targets “illegal 3rd party exploits, including open proxies, worms/viruses with built-in spam engines, virus-infected PCs & servers and other types of trojan-horse exploits.” That is to say it is a list of known open proxies and exploited computers being used to send spam and viruses. The XBL includes information gathered by Spamhaus as well as by other contributing DNSBL operations such as the Composite Blocking List (CBL).
The Policy Block List (PBL)[11] is similar to a Dialup Users List. The PBL lists not only dynamic IP addresses but also static addresses that should not be sending email directly to third-party servers. Examples of such are an ISP’s core routers, corporate users required by policy to send their email via company servers, and unassigned IP addresses. Much of the data is provided to Spamhaus by the organizations that control the IP address space, typically ISPs.
The Domain Block List (DBL)[12] was released in March 2010 and is a list of domain names, which is both a domain URI Blocklist and RHSBL. It lists spam domains including spam payload URLs, spam sources and senders (“right-hand side”), known spammers and spam gangs, and phish, virus and malware-related sites. It later added a zone of “abused URL shortners”, a common way spammers insert links into spam emails.
The Botnet Controller List (BCL)[13] was released in June 2012 and is a list of IP addresses. It lists IP addresses of which Spamhaus believes to be operated by cybercriminals for the exclusive purpose of hosting botnet Command&Control infrastructure. Such infrastructure is commonly used by cybercriminals to control malware infected computers.
The Composite SnowShoe (CSS)[14] is an automatically produced dataset of IP addresses that are involved in sending low-reputation email. Listings can be based on HELO greetings without an A record, generic looking rDNS or use of fake domains, which could indicate spambots or server misconfiguration. CSS is part of SBL.
The Spamhaus White List (SWL)[15] was released in October 2010 and was a whitelist of IPv4 and IPv6 addresses. The SWL was intended to allow mail servers to separate incoming email traffic into 3 categories: Good, Bad and Unknown. Only verified legitimate senders with clean reputations were approved for whitelisting and there were strict terms to keeping a Spamhaus Whitelist account.
The Domain White List (DWL)[15] was released in October 2010 and was a whitelist of domain names. The DWL enables automatic certification of domains with DKIM signatures. Only verified legitimate senders with clean reputations were approved for whitelisting and there are strict terms to keeping a whitelist account.
Spamhaus also provides two combined lists. One is the SBL+XBL[16] and the second is called ZEN,[17] which combines all the Spamhaus IP address-based lists.
Register of Known Spam Operations [ edit ]
The Spamhaus Register of Known Spam Operations (ROKSO) is a database of spammers and spam operations who have been terminated from three or more ISPs due to spamming. It contains publicly sourced information about these persons, their domains, addresses and aliases.[18]
The ROKSO database allows ISPs to screen new customers, ensuring that ROKSO-listed spammers find it difficult to get hosting.[19] A listing on ROKSO also means that all IP addresses associated with the spammer (his other domains, sites, servers, etc.) get listed on the Spamhaus SBL as “under the control of a ROKSO-listed spammer” whether there is spam coming from them or not (as a preemptive measure).
There is a special version of ROKSO, available to Law Enforcement Agencies, containing data on hundreds of spam gangs, with evidence, logs and information on illegal activities of these gangs, too sensitive to publish in the public part of ROKSO.
Don’t Route Or Peer list [ edit ]
The Spamhaus Don’t Route Or Peer (DROP) List is a text file delineating CIDR blocks that have been stolen or are otherwise “totally controlled by spammers or 100% spam hosting operations”.[20] As a small subset of the SBL, it does not include address ranges registered to ISPs and sublet to spammers, but only those network blocks wholly used by spammers. It is intended to be incorporated in firewalls and routing equipment to drop all network traffic to and from the listed blocks.[20] The DROP webpage FAQ[21] states the data is free for all to download and use. In 2012 Spamhaus offered a BGP feed of the same DROP data.
Companies [ edit ]
The Spamhaus Group consists of a number of independent companies which focus on different aspects of Spamhaus anti-spam technology or provide services based around it. At the core is The Spamhaus Project SLU,[22] a not-for-profit company based in Andorra which tracks spam sources and cyber threats such as phishing, malware and botnets and publishes free DNSBLs. Commercial services are managed by a British data delivery company Spamhaus Technology Ltd.,[23] based in London UK which manages data distribution services for large scale spam filter systems.
Awards [ edit ]
National Cyber Forensics Training Alliance 2008 Cyber Crime Fighter Award [24]
Internet Service Providers Association’s Internet Hero of 2003 Award [25]
Greatest Contribution to anti-spam in the last 10 years presented to Spamhaus by Virus Bulletin Magazine.[26]
Conflicts [ edit ]
e360 lawsuit [ edit ]
In September 2006, David Linhardt, the owner-operator of American bulk-emailing company “e360 Insight LLC”,[4] filed suit against Spamhaus in Illinois for blacklisting his mailings. Spamhaus had the case moved from the state court to the U.S. Federal District Court for the Northern District of Illinois and asked to have the case dismissed for lack of jurisdiction.[27][28] The court, presided over by Judge Charles Kocoras, proceeded with the case against Spamhaus without considering the jurisdiction issue, prompting British MP Derek Wyatt to call for the judge to be suspended from office.[29] Not having had its objection to jurisdiction examined, Spamhaus refused to participate in the U.S. case any further and withdrew its counsel. However, Spamhaus was deemed by the court to have “technically accepted jurisdiction” by having initially responded at all, and the judge, angry at Spamhaus having walked out of his court, awarded e360 a default judgement totaling US$11,715,000 in damages. Spamhaus subsequently announced that it would ignore the judgement because default judgements issued by U.S. courts without a trial “have no validity in the U.K. and cannot be enforced under the British legal system”.[30][31]
Following the ruling in its favour, e360 filed a motion to attempt to force ICANN to remove the domain records of Spamhaus until the default judgement had been satisfied.[28] This raised international issues regarding ICANN’s unusual position as an American organization with worldwide responsibility for domain names,[32][33] and ICANN protested[34] that they had neither the ability nor the authority to remove the domain records of Spamhaus, which is a UK-based company. On 20 October 2006, Judge Kocoras issued a ruling denying e360’s motion against ICANN, stating in his opinion that “there has been no indication that ICANN [is] not [an] independent entit[y] [from Spamhaus], thus preventing a conclusion that [it] is acting in concert” with Spamhaus and that the court had no authority over ICANN in this matter. The court further ruled that removing Spamhaus’s domain name registration was a remedy that was “too broad to be warranted in this case”, because it would “cut off all lawful online activities of Spamhaus via its existing domain name, not just those that are in contravention” of the default judgment. Kocoras concluded, “[w]hile we will not condone or tolerate noncompliance with a valid order of this court [i.e., Spamhaus’ refusal to satisfy the default judgement] neither will we impose a sanction that does not correspond to the gravity of the offending conduct”.[35][36]
In 2007, Chicago law firm Jenner & Block LLP took up Spamhaus’s case pro bono publico and appealed the ruling. The U.S. federal Court of Appeals for the Seventh Circuit vacated the damages award and remanded the matter back to the district court for a more extensive inquiry to determine damages. In January 2008, e360 Insight LLC filed for bankruptcy and closed down, citing astronomical legal bills associated with this court case as the reason for its demise.[37]
In 2010, Judge Kocoras reduced the $11.7 million damages award to $27,002[38]—$1 for tortious interference with prospective economic advantage, $1 for claims of defamation, and $27,000 for “existing contracts”.[39]
Both parties appealed, but e360’s case for increasing the damages was sharply criticized by Judge Richard Posner of the Seventh Circuit: “I have never seen such an incompetent presentation of a damages case,” Posner said. “It’s not only incompetent, it’s grotesque. You’ve got damages jumping around from $11 million to $130 million to $122 million to $33 million. In fact, the damages are probably zero.”[40] On 2 September 2011 the court reduced the damages award to just $3 total, and ordered the plaintiff e360 to pay the costs of the appeal for the defence.[41]
Spamhaus versus nic.at [ edit ]
In June 2007, Spamhaus requested the national domain registry of Austria, nic.at, to suspend a number of domains, claiming they were registered anonymously by phishing gangs for illegal bank phishing purposes.[42] The registry nic.at rejected the request and argued that they would break Austrian law by suspending domains, even though the domains were used for criminal purposes, and demanded proof that the domains were registered under false identities.[42][43] For some time the domains continued to phish holders of accounts at European banks. Finally, Spamhaus put the mail server of nic.at on their SBL spam blacklist under the SBL’s policy “Knowingly Providing a Spam Support Service for Profit” for several days which caused interference of mail traffic at nic.at.[43] All of the phishing domains in question have been since deleted or suspended by their DNS providers.[42][44]
Blocking of Google Docs IPs [ edit ]
In August 2010, Spamhaus added some Google-controlled IP addresses used by Google Docs to its SBL spam list, due to Google Docs being a large source of uncontrolled spam. Google quickly fixed the problem and Spamhaus removed the listing. Though initially wrongly reported by some press to be IPs used by Gmail, later it was clarified that only Google Docs was blocked.[45]
CyberBunker dispute and DDoS attack [ edit ] [46][47] Diagram showing the role of open resolvers, improperly configured servers vulnerable to IP address spoofing
In March 2013, CyberBunker, an internet provider named after its former headquarters in a surplus NATO bunker in the Netherlands[48] that “offers anonymous hosting of anything except child porn and anything related to terrorism”[49] was added to the Spamhaus blacklist used by email providers to weed out spam.[50] Shortly afterwards, beginning on March 18,[51] Spamhaus was the target of a distributed denial of service (DDoS) attack exploiting a long-known vulnerability in the Domain Name System (DNS) which permits origination of massive quantities of messages at devices owned by others using IP address spoofing.[52][53] Devices exploited in the attack may be as simple as a cable converter box connected to the internet.[54] The attack was of a previously unreported scale (peaking at 300 Gbit/s; an average large-scale attack might reach 50 Gbit/s, and the largest previous publicly reported attack was 100 Gbit/s) was launched against Spamhaus’s DNS servers; as of 27 March 2013 the effects of the attack had lasted for over a week. Steve Linford, chief executive for Spamhaus, said that they had withstood the attack, using the assistance of other internet companies such as Google to absorb the excess traffic. Linford also claimed that the attack was being investigated by five different national cyber-police-forces around the world, who had chosen to remain anonymous to avoid similar attacks on their own infrastructure.[55] Spamhaus also hired Cloudflare, a DDoS mitigation company, to assist them by distributing their internet services across Cloudflare’s worldwide network,[56] after which the focus of the attack was redirected to the companies that provide Cloudflare’s network connections.[50]
Spamhaus alleged that CyberBunker, in cooperation with “criminal gangs” from Eastern Europe and Russia, was behind the attack; CyberBunker did not respond to the BBC’s request for comment on the allegation;[55] however, Sven Olaf Kamphuis, the owner of CyberBunker, posted to his Facebook account on 23 March “Yo anons, we could use a little help in shutting down illegal slander and blackmail censorship project ‘spamhaus.org,’ which thinks it can dictate its views on what should and should not be on the Internet.”[48] According to The New York Times Kamphuis also claimed to be the spokesman of the attackers, and said in a message “We are aware that this is one of the largest DDoS attacks the world had publicly seen”, and that CyberBunker was retaliating against Spamhaus for “abusing their influence”. The NYT added that security researcher Dan Kaminsky said “You can’t stop a DNS flood … The only way to deal with this problem is to find the people doing it and arrest them”.[50]
The attack was attributed by network engineers to an anonymous group unhappy with Spamhaus,[50] later identified by the victims of the attack as Stophaus,[48] a loosely organized group of “bulletproof spam and malware hosters”.[57]
On 26 April 2013, the owner of CyberBunker, Sven Olaf Kamphuis, was arrested in Spain for his part in the attack on Spamhaus. He was held in jail for 55 days pending extradition to the Netherlands, was released pending trial, and was ultimately found guilty and sentenced to 240 days in jail, with the remaining days suspended.[58][59]
The British National Cyber Crime Unit revealed that a London schoolboy had been secretly arrested as part of a suspected organised crime gang responsible for the DDoS attacks.[60] A briefing document giving details of the schoolboy’s alleged involvement states: “The suspect was found with his computer systems open and logged on to various virtual systems and forums. The subject has a significant amount of money flowing through his bank account. Financial investigators are in the process of restraining monies.”
Ames v. The Spamhaus Project Ltd [ edit ]
In 2014, Spamhaus was sued by California-based entrepreneurs Craig Ames and Rob McGee, who were involved with a bulk email marketing services business, initially through a US corporation called Blackstar Media LLC, and later as employees of Blackstar Marketing, a subsidiary of the English company Adconion Media Group Limited, which bought Blackstar Media in April 2011. Although an initial motion by Spamhaus to strike out the claims failed,[61] they ultimately prevailed when the claimants dropped their case and paid Spamhaus’ legal costs.[62]
See also [ edit ]
References [ edit ]
키워드에 대한 정보 스팸 하우스
다음은 Bing에서 스팸 하우스 주제에 대한 검색 결과입니다. 필요한 경우 더 읽을 수 있습니다.
이 기사는 인터넷의 다양한 출처에서 편집되었습니다. 이 기사가 유용했기를 바랍니다. 이 기사가 유용하다고 생각되면 공유하십시오. 매우 감사합니다!
사람들이 주제에 대해 자주 검색하는 키워드 IP 양식 블랙리스트를 제거하는 방법 | 스팸하우스 | CBL | 2022년 업데이트됨
- How to remove IP from blacklist
- how to remove ip from spamhaus
- how to remove ip from cbl
- ip address blocked
- whitelist ip address
- sorbs spam blacklist removal
- spamhaus blacklist removal
- cbl blacklist removal
- mxtoolbox blacklist removal
- spamhaus zen blacklist removal
- how to unblock ip address
- remove ip from blacklist
- remove ip from spamhaus
- remove ip from cbl
- blacklist removal
- ip blacklist removal
- how to remove ip from google blacklist
- website blacklist check
IP #양식 #블랙리스트를 #제거하는 #방법 #| #스팸하우스 #| #CBL #| #2022년 #업데이트됨
YouTube에서 스팸 하우스 주제의 다른 동영상 보기
주제에 대한 기사를 시청해 주셔서 감사합니다 IP 양식 블랙리스트를 제거하는 방법 | 스팸하우스 | CBL | 2022년 업데이트됨 | 스팸 하우스, 이 기사가 유용하다고 생각되면 공유하십시오, 매우 감사합니다.
